The ISO 27001 Standard.
And How An ISMS (Information Security Management System) Works.
Table of contents
Why work with ISO 27001 and have an ISMS?
Your company and organization store valuable information; you need a defence system to protect it from cyber threats. ISO 27001 is the blueprint for building and maintaining that defence system, the Information Security Management System (ISMS).
But how do you get started? What are the ISO 27001 requirements? What’s involved in becoming compliant with ISO 27001, and how can it benefit your business?
Let’s guide you through ISO 27001, starting with essential knowledge and ending with how to achieve compliance and finally prepare for certification. Along the way, we’ll show how a connected compliance approach makes this journey smoother, faster, and more efficient.
At the end of the page, we have provided a list of 4 actionable takeaways you should always consider when working with ISO 27001 compliance.
What is ISO 27001?
ISO 27001 is like a rulebook for protecting sensitive information. It’s an international standard that outlines how an organization should set up and maintain an Information Security Management System (ISMS) — a framework designed to manage and minimize risks to information.
Imagine your organization’s security strategy as a living, breathing organism. It must adapt to your business's changing needs and cybersecurity landscape. That’s where ISO 27001 comes in: it doesn’t give you a one-size-fits-all solution but instead allows you to tailor your security measures according to your specific risks and enables you to be agile and resilient.
A Brief History of ISO 27001
ISO 27001 was created in 2005 and has evolved since then. The latest 2022 revision introduces new methods to strengthen your organization's security by making risk management more flexible and incorporating better monitoring tools.
ISO 27001 is closely related to ISO 27002, an instruction manual that provides guidelines for selecting your organisation's proper security controls.
Why ISO 27001 matters to your organization
Why should you care about ISO 27001? Protecting your data isn’t just about avoiding fines or passing audits – it’s about trust and reputation, efficiency, and constant improvement.
-
Trust and reputation: Achieving ISO 27001 compliance shows your clients and partners that you take security seriously. It’s a badge of confidence that assures everyone you do business with that their information is safe in your hands.
-
Efficiency: By aligning your security controls with your organisation's ongoing risks, you ensure your resources are used wisely. There is no wasted effort, just streamlined, focused security measures.
-
Continual improvement: ISO 27001 requires continuous assessment and improvement of security processes. This is not a one-time event but an evolving strategy that helps you avoid potential threats.
How to get started with ISO 27001: First steps towards compliance
Like any significant business project, it begins with careful planning and ensuring commitment from the right people. Below, we’ll walk you through the key first steps to get your organization to ISO 27001 compliance. However, this is a short overview of the deliverables that you should have in place:
-
Management Commitment: Whether through a business case or direct approval, management must be fully engaged and ready to support the process.
-
Presentation Meeting: Arrange a meeting with top management to go over the project plan, roles, and any analysis of internal/external factors that might influence your ISMS.
-
Action Plan: After securing management’s buy-in, you’ll need a detailed action plan outlining the tasks and timelines for implementing ISO 27001.
1. Determine if your organization needs ISO 27001
The first question to answer is whether your organization needs to work with ISO 27001. This isn’t just a box to tick—it’s about aligning your security needs with your business goals. Ask yourself:
- Does your organization handle sensitive information that needs to be protected?
- Are there regulatory requirements or client demands that necessitate strong information security measures?
- Does your organization face more complex regulatory demands beyond ISO 27001? Consider additional frameworks, such as NIS2, GDPR, DORA, CSRD or other standards that could impact your compliance strategy and influence the scope of your ISMS.
- Would ISO 27001 certification give your business a competitive advantage or improve customer trust?
Answering these questions can help determine if ISO 27001 is the correct standard. For many organizations, the benefits of implementing an ISMS far outweigh the costs, mainly if you handle confidential or sensitive data.
2. Ensure Commitment from Management
A successful ISO 27001 implementation hinges on the support and involvement of your top management. Without their buy-in, allocating the necessary resources and making the changes needed to comply with the standard can be difficult.
But how do you get management on board, especially if they’re not fully engaged in compliance or information security?
- Prepare a business case: If your management isn’t fully aware of the importance of information security, you might need to make a business case for why ISO 27001 is essential. Our GRC platform provides a business case template that you can customize to highlight the strategic importance of an ISMS.
Focus on the following points:- How the ISMS aligns with your business strategy (confidentiality, integrity, and data availability).
- Tangible business benefits include competitive advantage, increased customer trust, or operational efficiency.
- How long will the implementation take based on a project plan?
- A cost estimate covers internal resources and any external support you might need.
- If management is already onboard: If your management already sees the value of ISO 27001 and an ISMS, you can skip the business case and outline the implementation plan. Ensure they understand their role in supporting the ISMS project.
3. Plan your ISO 27001 implementation
Once you’ve secured management’s commitment, the next step is planning. Here’s what you need to consider:
-
Call for a presentation meeting: Gather top management and relevant stakeholders for a presentation that outlines the ISO 27001 implementation process. Use this meeting to present your business case or walk them through the project plan.
-
Discuss internal and external factors: If you plan on becoming certified, it’s essential to analyze the internal and external factors that could impact your ISMS. This includes understanding risks within and outside your organization that might affect security measures. Our platform consists of a template for this analysis, which is mandatory if you aim for certification.
-
Assign roles and responsibilities: During the presentation, ensure management understands what’s expected of them throughout the implementation process. For example, they must appoint key roles, such as the ISMS and risk owners.
Achieving ISO 27001 compliance
Once you understand ISO 27001, the next step is completing full compliance. This is where the power of “connected compliance” makes your journey more manageable.
A GRC platform is designed to minimize compliance burden by connecting all the necessary components—such as risk management, incident management, and vendor management—into one seamless system.
But first, let’s start by looking at the ISO 27001 requirements and putting them into context.
Understanding ISO 27001 Requirements
To achieve and maintain ISO 27001 certification, organizations must meet a series of defined requirements that ensure a comprehensive and effective Information Security Management System (ISMS). These requirements establish the foundational practices that guide your security framework and provide ongoing risk management, data protection, and compliance with the standard.
Core Components of ISO 27001 Requirements
The primary ISO 27001 requirements are outlined in 10 clauses (sections) and Annex A, which contains a detailed list of security controls. Here's a breakdown of some of the critical aspects:
Context of the Organization
Organizations must understand the internal and external issues that can affect their ISMS, identify interested parties (such as stakeholders and regulators), and determine the scope of their ISMS to ensure it aligns with the business's specific security needs.
Leadership and Commitment
Top management must be fully involved in the implementation of ISMS. This requirement emphasizes leadership's role in demonstrating commitment to information security, establishing the security policy, and assigning roles and responsibilities to support the ISMS.
Risk Assessment and Treatment
A critical element of ISO 27001 is performing a comprehensive risk assessment to identify potential threats and vulnerabilities. Organizations must then establish a risk treatment plan that applies the appropriate security controls from Annex A or other relevant sources.
Support and Resources
The standard requires organizations to provide the necessary resources for their ISMS, including employee training and awareness, effective communication channels, and proper documentation management to ensure the ISMS runs smoothly.
Operation and Control Implementation
ISO 27001 mandates implementing and documenting all necessary controls and processes to mitigate identified risks. This includes developing operational procedures, incident response plans, and monitoring mechanisms that align with business goals.
Performance Evaluation
Continual monitoring and evaluation of the ISMS's performance is required through internal audits, regular reviews, and periodic assessments of compliance and effectiveness. This ensures that any areas for improvement are identified and addressed.
Continual Improvement
ISO 27001 emphasizes a cycle of continuous improvement (Plan-Do-Check-Act) to ensure that the ISMS adapts to evolving security threats, business changes, and regulatory requirements.
Annex A Controls
Annex A contains a catalogue of security controls grouped into 4 overall categories:
- Organizational controls
- People controls
- Physical controls
- Technological controls
Organizations must select and implement the controls that best mitigate their specific risks. These controls provide flexibility, ensuring the ISMS is tailored to each organization’s security challenges.
Navigating ISO 27001 Requirements with a GRC Platform
Managing ISO 27001 requirements can be a complex endeavor, but a connected GRC platform simplifies the process by providing centralized task management, automated risk assessments, and integrated compliance tracking. This ensures that your organization not only achieves compliance but also maintains a resilient and adaptable ISMS.
By understanding and adhering to the core ISO 27001 requirements, your organization is better positioned to protect sensitive information, build stakeholder trust, and continually improve its security posture.
How “Connected Compliance” simplifies ISO 27001 compliance
Think of it like building a puzzle. Instead of manually trying to fit each piece together, our GRC platform gives you the complete picture, automating the most tedious tasks and ensuring all the pieces are perfectly aligned. Let’s lay down the pieces together:
Task Management – The Annual Wheel or Project Plan
You can set up a project plan with structured Task Management, often called the "annual cycle." This tool helps you manage all recurring compliance tasks, ensuring that nothing falls through the cracks. Whether it’s scheduling audits, updating policies, or reviewing risks, the annual cycle keeps everyone on track, year after year.
Managing tasks without a dedicated tool typically involves using manual spreadsheets, email reminders, or calendars to track compliance activities. Teams often rely on individuals to remember deadlines, schedule audits, document changes, and update policies. While possible, this approach can lead to missed tasks, inconsistent follow-ups, and disjointed communication, making it harder to stay organized and ensure ongoing compliance. Task management becomes time-consuming, and the risk of errors or lapses increases without centralized automation and tracking.
Cross-Standard and Integrated Risk Management Made Simple
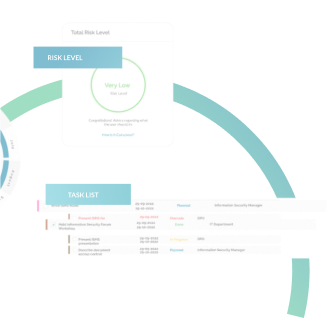
A key element of ISO 27001 is identifying and managing risks. An Integrated Risk Management tool simplifies this by helping you pinpoint potential security threats, assess their impact, and decide on appropriate controls. With a clear overview of your risk landscape, you can make informed decisions that protect your organization.
Information Security Incident Management
Even the best security plans face incidents from time to time. The crucial part is how efficiently you handle them. An Incident Management tool lets you document, track, and resolve incidents quickly, ensuring they don’t lead to more significant issues. Over time, this helps improve your overall security resilience.
Vendor Management
Managing vendor risks is essential in a world where third-party relationships are increasingly common. A Vendor Management tool helps you monitor your suppliers' compliance with security requirements, reducing the risk of breaches stemming from third parties.
Employee Awareness and Training
Your employees are your first line of defence. Ensuring they understand and follow your security protocols is critical. You can set up and track Employee Awareness programs in most ISMSs, ensuring everyone in your organization is educated on the latest security policies and best practices. Ongoing training helps reduce human error, one of the most common causes of security breaches.
Cross-Compliance Overview
Many organizations must comply with multiple standards, which can be overwhelming. However, with a Cross-Compliance Overview, managing compliance across various frameworks like ISO 27001, GDPR, NIS2, etc. has become easier. This tool provides a unified view of all your compliance requirements and progress, helps you align efforts, avoids duplication, and streamlines processes across different standards.
With these puzzle pieces, connected compliance turns the often complex journey toward ISO 27001 compliance into a manageable, efficient, and connected process we have mapped out for you. From determining the information security needs, strategising your work, tracking your cross-compliance performance, and getting to and maintaining your goal, an ISMS ensures you stay on top of everything with minimal manual effort. All of this is bound together with the visualisation in the cross-compliance overview and the extensive library of tasks, suggested solutions, and documents you need to complete. With NorthGRC, you can access all the templates you need to ensure compliance with ISO 27001. Go ahead and check out the NorthGRC platform here.
Best practices for compliance
Compliance isn’t just about meeting requirements; it’s about creating a security culture throughout your organization. By leveraging a GRC platform, you can:
- Continuously assess and monitor your information security posture.
- Use real-time dashboards to track compliance efforts.
- Automate critical tasks like risk assessments and incident reporting.
- Keep all your departments on the same page with unified security measures.
With connected compliance, staying compliant becomes less burdensome, leaving you more time to focus on other critical aspects of your business.
3. Preparing for ISO 27001 Certification
After laying a solid foundation with your ISMS and aligning your processes through compliance, certification is the final stage in your journey. Let’s dive deeper into why getting certified matters and the steps involved in achieving ISO 27001 certification.
H3: Why get ISO 27001 certified?
Certification is like a seal of approval, showing that your organization has gone above and beyond in meeting international security standards. It’s not just about protecting your data but demonstrating your commitment to security to clients, partners, and regulators.
Achieving ISO 27001 certification can:
- Boost trust and credibility: A certified ISMS reassures stakeholders that your organization follows a structured, internationally recognized approach to safeguarding information.
- Fulfil legal and contractual obligations: Many industries and clients demand ISO 27001 compliance as a baseline requirement for doing business, making certification essential to stay competitive.
- Reduce security incidents and associated costs: An ISMS can help your organization minimize risks, reducing the chances of data breaches, security incidents, and non-compliance penalties.
- Improve operational efficiency: Certification often leads to streamlined processes and better resource allocation, ensuring your security efforts are focused and effective.
The ISO 27001 certification process
Certification involves an external, independent auditor's comprehensive evaluation of your ISMS. The certification process is typically divided into three key stages:
Stage 1: Preliminary audit (Document Review)
This stage is a preliminary assessment where the auditor evaluates your documentation and ISMS policies to ensure they meet the requirements outlined in ISO 27001. The purpose is to check that you’ve established all the key elements of the ISMS and have adequately documented the procedures and controls.
Key activities include:
- Document review: The auditor will review your organization’s ISMS documentation, such as policies, procedures, risk assessments, and control implementations.
- Gap analysis: The auditor may conduct a gap analysis to identify areas where your ISMS doesn’t fully align with the ISO 27001 requirements. This step helps highlight any improvements needed before the formal certification audit.
At this stage, the auditor will provide feedback, highlighting areas that need more attention. This step is critical as it allows you to adjust before the entire audit.
Stage 2: Certification audit (On-site audit)
Once the documentation review is completed and any necessary changes have been made, the auditor will conduct a more in-depth, on-site audit. During this stage, the auditor assesses the practical implementation of your ISMS and ensures it’s functioning as documented.
Key activities include:
- ISMS performance evaluation: The auditor will observe how your organization’s ISMS works, verifying that security controls effectively manage risks and protect information. They may examine processes such as access control, incident management, and employee awareness.
- Interviews and evidence collection: The auditor will interview key personnel responsible for information security and collect evidence supporting the ISMS's functioning. This could include reviewing records, risk assessments, audit logs, and incident reports.
- Assessment of compliance with controls: The auditor will check whether the implemented controls align with your organization’s risk assessments and the requirements of ISO 27001.
Upon completing the audit, the auditor will compile a report highlighting non-conformities in areas where your organization doesn’t meet the requirements. If non-conformities are identified, you’ll be given a timeframe to address them before final approval.
Stage 3: Issuance of Certification
If the auditor concludes that your organization complies with the ISO 27001 standard, you will receive the ISO 27001 certification. This certification confirms that your ISMS meets the international requirements for information security management.
Key activities include:
- Certificate issuance: Once all non-conformities (if any) have been corrected, your organization will receive the official ISO 27001 certification, valid for three years.
- Public recognition: Certification allows you to promote your achievement to clients, partners, and regulators, enhancing your organization’s reputation as a trusted, security-conscious entity.
Ongoing monitoring and surveillance audits
ISO 27001 certification isn’t a one-time achievement - it requires continuous effort to maintain compliance. During the three-year certification period, your organization will undergo annual surveillance audits conducted by the certification body. These audits ensure that your ISMS continues to operate effectively and that improvements are being made as needed.
What happens during a surveillance audit?
- Review of ISMS performance: The auditor will review your ISMS’s ongoing performance, ensuring controls are still functioning and effective.
- Checking for continuous improvement: ISO 27001 requires constant improvement of the ISMS. The auditor will check how your organization addresses new risks, security incidents, and changes in the business environment.
- Addressing non-conformities: Any minor non-conformities identified during the initial or subsequent audits will be reviewed to ensure they have been properly resolved.
Surveillance audits are typically less comprehensive than the initial certification but are vital for maintaining certification and ensuring your organization’s security posture remains robust.
Maintaining ISO 27001 Certification
Achieving ISO 27001 certification is a significant milestone, but it’s only the start of your organization’s information security journey. Once certified, you must actively maintain your ISMS to keep it compliant with ISO 27001 requirements and improve security practices over time.
Here’s what maintaining an ISO 27001 certification involves:
- Ongoing monitoring and internal audits
Regular internal audits ensure your controls function effectively, identify non-conformance areas, and help mitigate emerging risks. Surveillance audits conducted by the certification body also occur annually to verify that your ISMS meets the standard's requirements. - Continual improvement
ISO 27001 requires that organizations continually improve their ISMS. This means fixing gaps identified during audits and proactively enhancing security measures. As new technologies, threats, and business needs emerge, your ISMS should evolve to ensure it effectively mitigates risks and secures sensitive data. - Incident management and response
Maintaining your certification requires demonstrating that your organization can respond swiftly and effectively to security incidents. Using an effective Incident Management system, you can track, manage, and resolve incidents, learning from them to strengthen your ISMS. Regularly reviewing these incidents ensures that your ISMS adapts to new challenges, helping you avoid repeated issues. - Risk management updates
The risk landscape isn’t static. You must regularly reassess the risks to your organization and update your risk management process accordingly. This includes identifying new threats, adjusting controls, and evaluating the effectiveness of your risk treatment plans. - Training and employee awareness
As part of your ongoing maintenance, your employees need continuous training on the latest security policies and best practices. Ensuring high levels of employee awareness about information security reduces the risk of breaches due to human error. - Adapting to regulatory and business changes
As regulations evolve (e.g., GDPR, NIS2), so must your ISMS. It is crucial to stay informed about changes to compliance requirements and align your ISMS with new regulations. It is essential to know that a dedicated management system like NorthGRC will automatically keep you updated on the latest developments. - Retaining management commitment
Top management must review ISMS performance, allocate resources, and support continuous improvement efforts. Without their engagement, the ISMS can become stagnant, risking your certification and every benefit related to that certification.
Maintaining ISO 27001 certification involves regular monitoring, proactive improvements, and a commitment to adapting to your business and regulatory environment changes. By staying vigilant and engaged, your organization can ensure long-term security and compliance success.
Actionable Takeaways For Your ISO 27001 Compliance Work
Achieving ISO 27001 compliance may seem daunting, but breaking it down into key steps can simplify your journey and ensure success. By focusing on strategic management engagement, clear goal-setting, thorough risk assessment, and leveraging the right tools, your organization can build and maintain a robust Information Security Management System (ISMS). Here are four essential, actionable takeaways to guide your compliance efforts:
Secure Management Buy-In
This is foundational, as management support ensures access to necessary resources and organizational alignment, making any compliance effort achievable.
Set Clear and Attainable Goals and Expectations
Establishing realistic objectives and milestones keeps your compliance efforts on track and helps measure progress.
Conduct a Gap and Risk Assessment
This is crucial for identifying existing weaknesses and risks within your organization and providing a roadmap for remediation and risk mitigation.
Use a GRC Platform to Streamline Your Compliance Work
Leveraging a GRC platform enhances efficiency, automates tedious tasks, and ensures a holistic and organized approach to compliance.
Learn more about
Governance, Risk, and Compliance
Subscribe and receive educational white papers, articles, and invites for our webinars and other events. The topics are always related to GRC.


.png)
